Facebook Spying Explained
November 17, 2011 1 Comment
Besides being a child of In-Q-Tel, a CIA front company, Facebook is also financed in part by Microsoft, Goldman Sachs, Hong Kong magnate Sir Ka-shing Li and venture capitalist Peter Andreas Thiel.
by Byron Acohido
USAToday
November 17, 2011
In recent weeks, Facebook has been wrangling with the Federal Trade Commission over whether the social media website is violating users’ privacy by making public too much of their personal information.

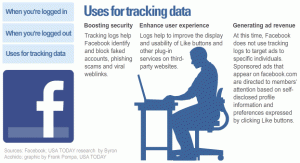
This is how Facebook spies on you. Click to enlarge. Image: USAToday
Far more quietly, another debate is brewing over a different side of online privacy: what Facebook is learning about those who visit its website.
Facebook officials are now acknowledging that the social media giant has been able to create a running log of the web pages that each of its 800 million or so members has visited during the previous 90 days. Facebook also keeps close track of where millions more non-members of the social network go on the Web, after they visit a Facebook web page for any reason.
To do this, the company relies on tracking cookie technologies similar to the controversial systems used by Google, Adobe, Microsoft, Yahoo and others in the online advertising industry, says Arturo Bejar, Facebook’s engineering director.
Facebook’s efforts to track the browsing habits of visitors to its site have made the company a player in the “Do Not Track” debate, which focuses on whether consumers should be able to prevent websites from tracking the consumers’ online activity.

If they happen to miss you the first way, they have a back up plan. Click to enlarge.
For online business and social media sites, such information can be particularly valuable in helping them tailor online ads to specific visitors. But privacy advocates worry about how else the information might be used, and whether it might be sold to third parties.
New guidelines for online privacy are being hashed out in Congress and by the World Wide Web Consortium, which sets standards for the Internet.
If privacy advocates get their way, consumers soon could be empowered to stop or limit tech companies and ad networks from tracking them wherever they go online. But the online advertising industry has dug in its heels, trying to retain the current self-regulatory system.
Online tracking involves technologies that tech companies and ad networks have used for more than a decade to help advertisers deliver more relevant ads to each viewer. Until now, Facebook, which makes most of its profits from advertising, has been ambiguous in public statements about the extent to which it collects tracking data.
And the third weapon used for spying by a social network is this one. Click to enlarge.
It contends that it does not belong in the same camp as Google, Microsoft and the rest of the online ad industry’s major players. Facebook CEO Mark Zuckerberg made this point to interviewer Charlie Rose on national TV last week.
For the past several weeks, Zuckerberg and other Facebook officials have sought to distinguish how Facebook and others use tracking data. Facebook uses such data only to boost security and improve how “Like” buttons and similar Facebook plug-ins perform, Bejar told USA TODAY. Plug-ins are the ubiquitous web applications that enable you to tap into Facebook services from millions of third-party web pages.
Facebook spokesman Andrew Noyes says the company has “no plans to change how we use this data.” He also says the company’s intentions “stand in stark contrast to the many ad networks and data brokers that deliberately and, in many cases, surreptitiously track people to create profiles of their behavior, sell that content to the highest bidder, or use that content to target ads.”
Conflicting pressures
Rather than appease its critics, Facebook’s public explanations of how it tracks and how it uses tracking data have touched off a barrage of questions from technologists, privacy advocates, regulators and lawmakers around the world.
“Facebook could be tracking users without knowledge or permission, which could be an unfair or deceptive business practice,” says Rep. Ed Markey, D-Mass., co-sponsor with Rep. Joe Barton, R-Texas, of a bill aimed at limiting online tracking of children.
The company “should be covered by strong privacy safeguards,” Markey says. “The massive trove of personal information that Facebook accumulates about its users can have a significant impact on them — now and into the future.”
Noting that “Facebook is the most popular social media website in the world,” Barton adds, “All websites should respect users’ privacy.”
After Zuckerberg appeared on the Charlie Rose TV show last week, Markey and Barton sent a letter to the 27-year-old CEO asking him to explain why Facebook recently applied for a U.S. patent for technology that includes a method to correlate tracking data with advertisements. They gave Zuckerberg a Dec. 1 deadline to reply.
“We patent lots of things, and future products should not be inferred from our patent application,” Facebook corporate spokesman Barry Schnitt says.
Facebook is under intense, conflicting pressures.
It must prove to its global financial backers that it is worthy of the hundreds of millions of dollars they’ve poured into the company, financial and tech industry analysts say. Those investors include Microsoft, Goldman Sachs, the Russian investment firm Digital Sky Technologies, Hong Kong financier Sir Ka-shing Li and venture capitalist Peter Andreas Thiel.
You may also want to read:
Invasive Cyber Technologies and Internet Privacy
Facebook & Social Media: A Convenient Cover For Spying
Read Full Article…

